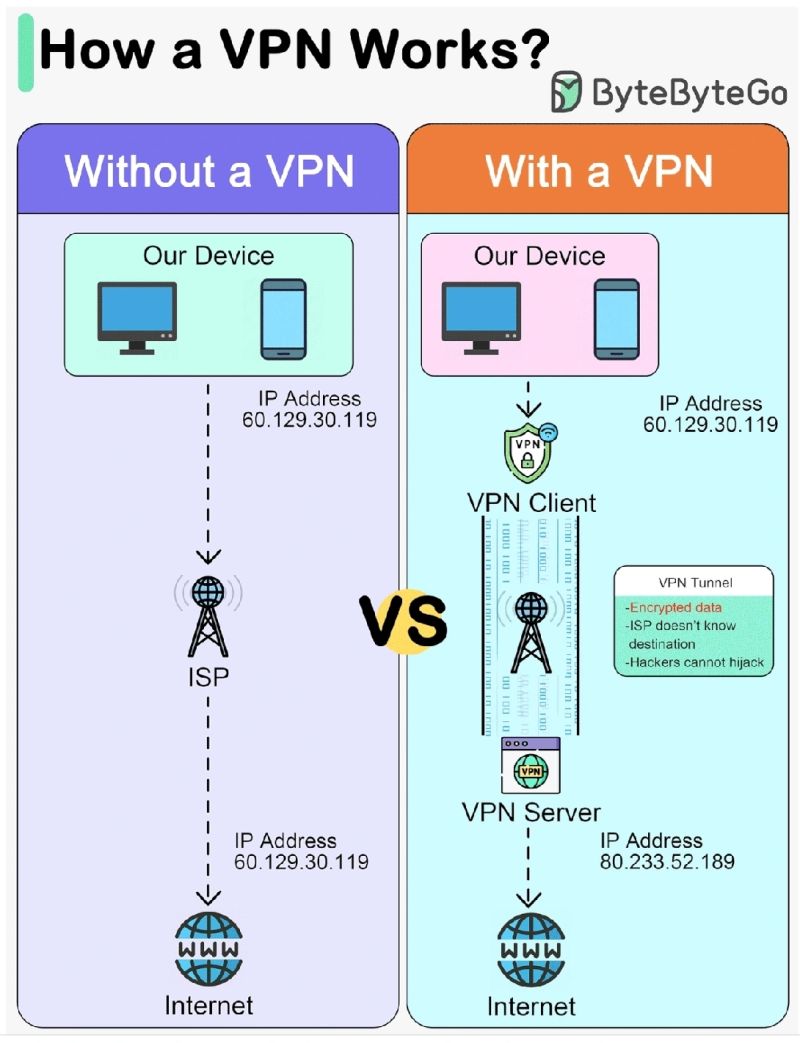
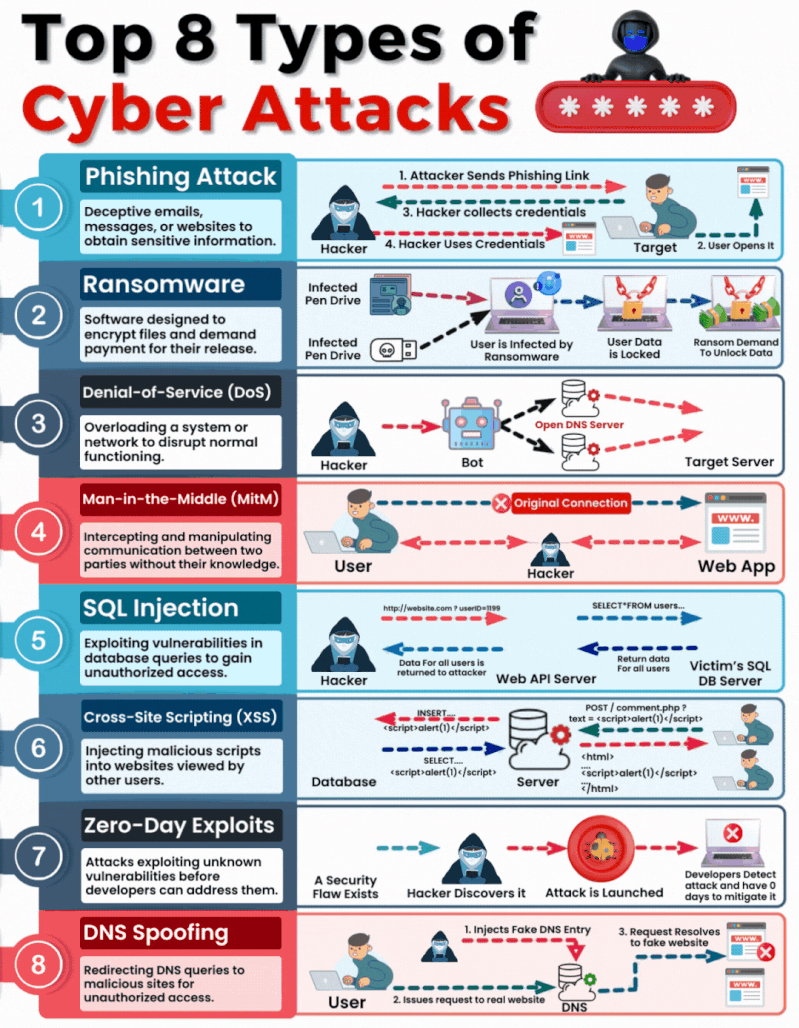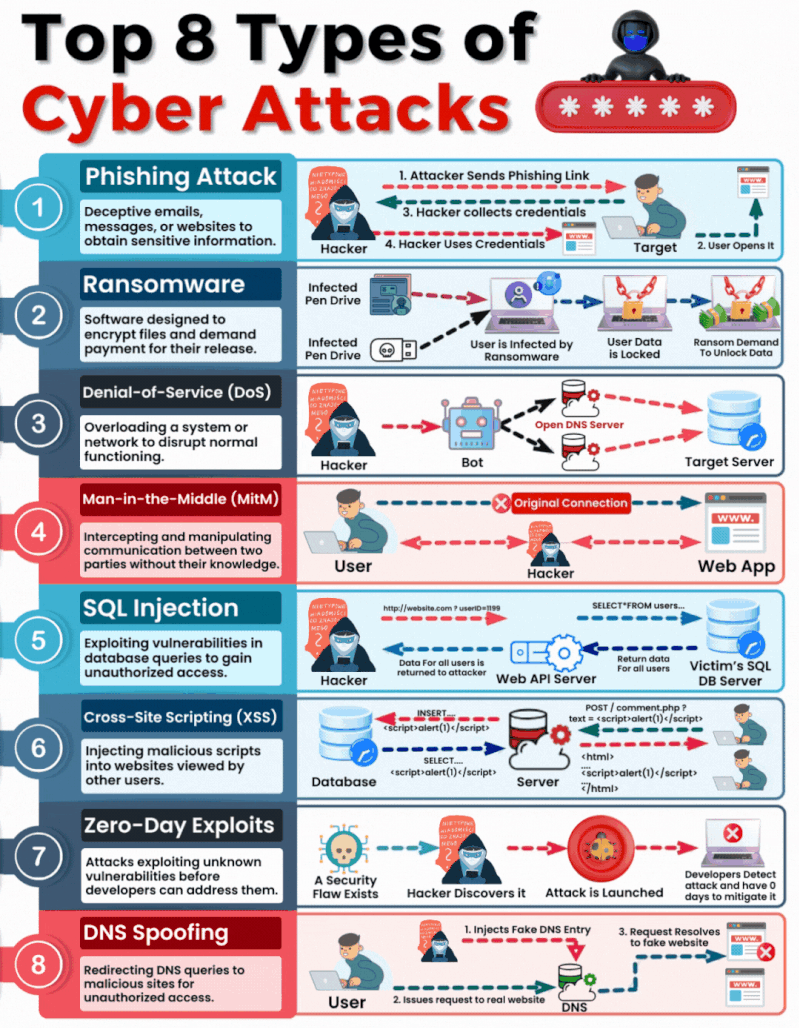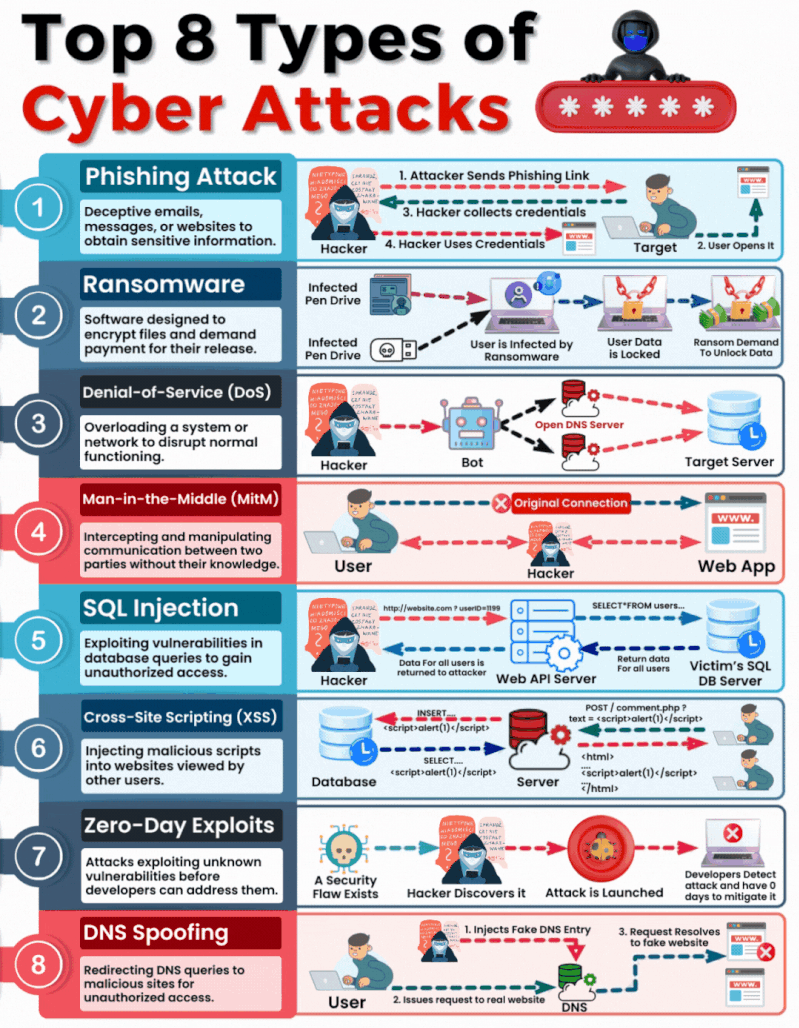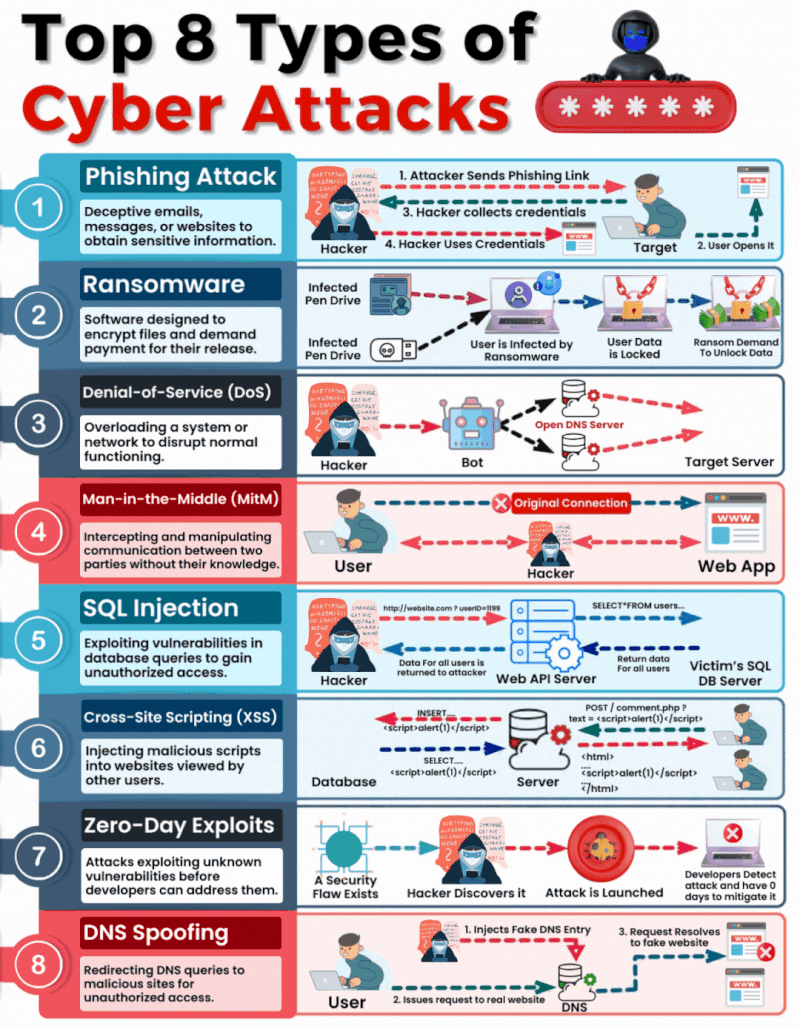
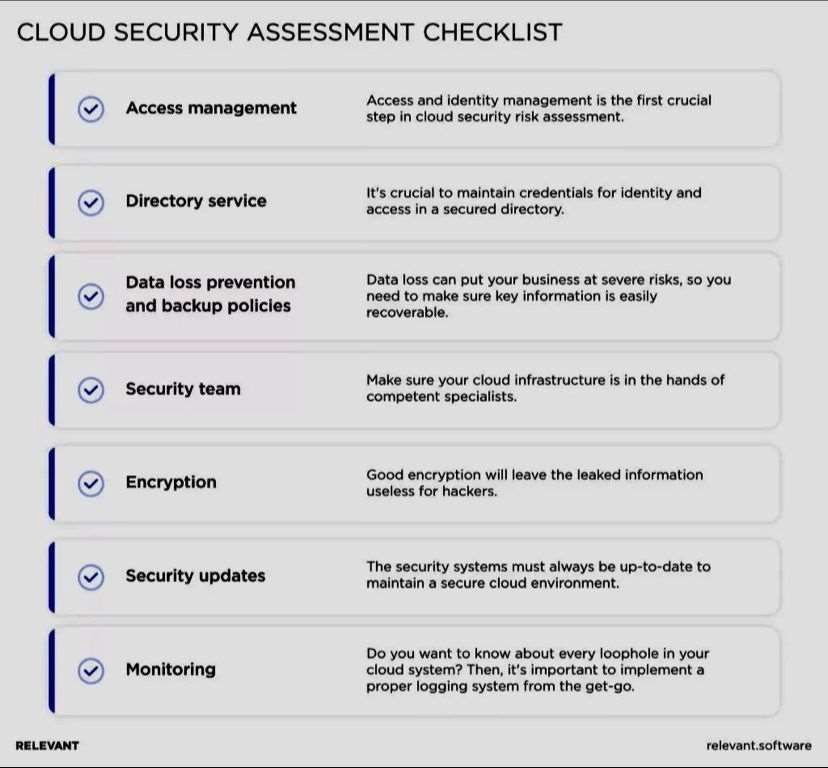
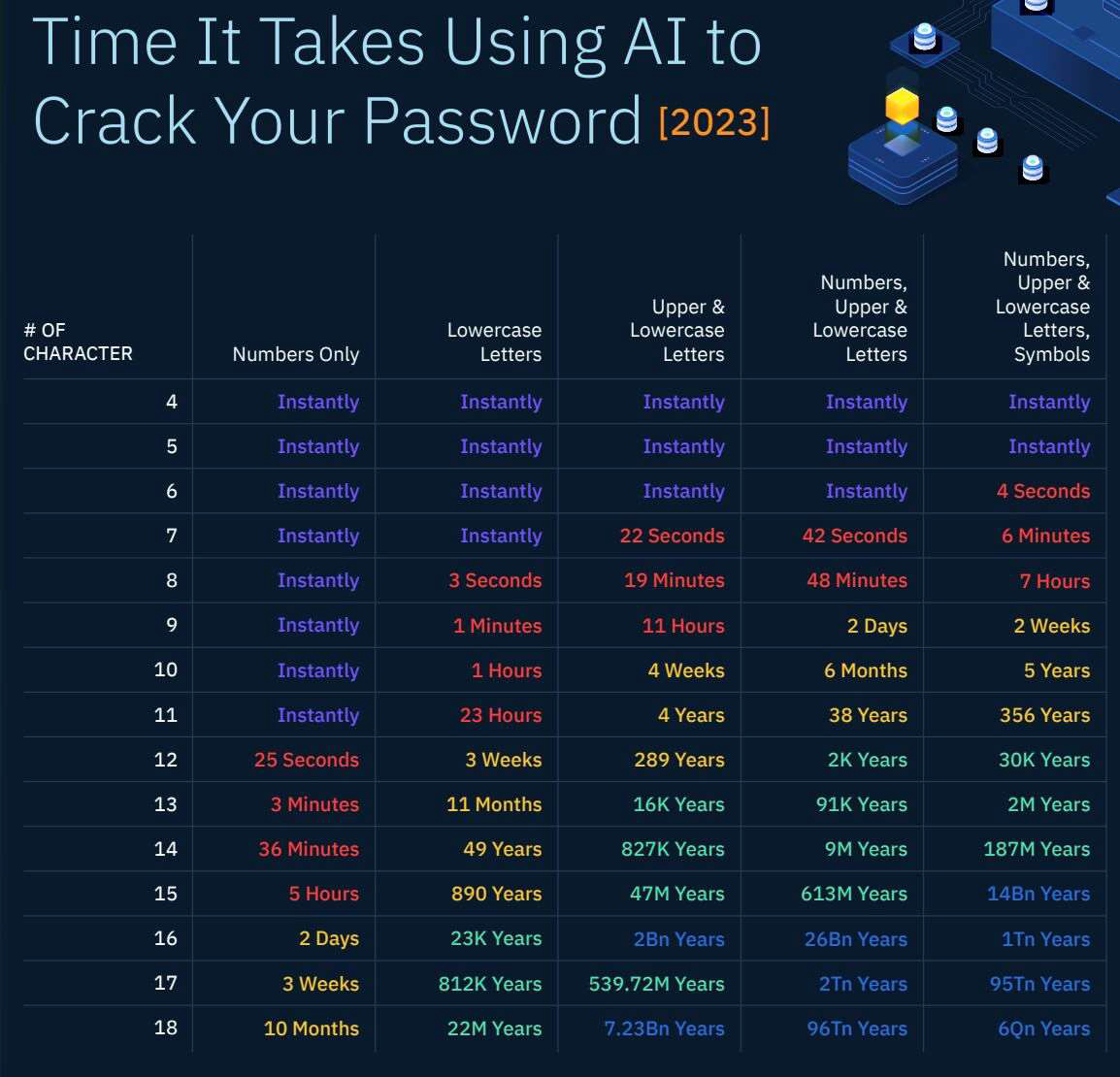
Insecure Vs. Secure Ports
Photo Credit Goes to Cyber Writes Disclaimer – This post has only been shared for an educational and knowledge-sharing purpose related to Technologies. Information was obtained from the source above source. All rights and credits are reserved for the respective owner(s). Keep learning and keep growing Source: LinkedIn Credits: Cyber Writes