Cloud Security Assessment Checklist

Cloud Security Assessment Checklist
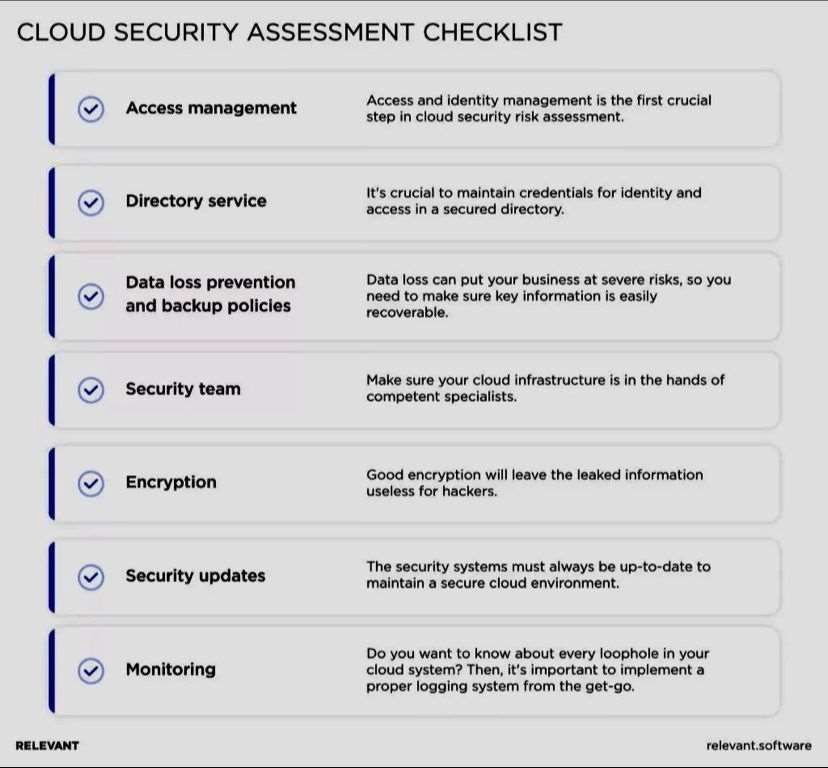
🔶Access management
🔹Who has access to your cloud system?
🔹What devices can access the system?
🔹Do you allow guests to access the cloud account?
🔹What permissions do guest accounts have?
🔹Is multi-factor authentication enabled (and does it have at least two steps)?
🔶Directory service
🔹Do you have an LDAP-compliant directory to keep the identities?
🔹How often do you update security protocols for this directory in a way that leverages the latest technologies and practices?
🔹Are security specialists who manage this directory adequately vetted?
🔶Data loss prevention and backup policies
🔹Do you have a comprehensive recovery plan?
🔹Does your provider have a default data backup functionality?
🔹Does your cloud environment support third-party data backup software?
🔹What are the existing plans and procedures for data recovery (physical storage locations, local area networks, cloud backup, and other solutions)?
🔹Do you perform regular check-ups of these physical storages and supplementary cloud
infrastructures?
🔶Security team
🔹Is the security team properly trained?
🔹Does a senior cloud security specialist at your company have relevant experience?
🔹Did the security team incorporate a proper cloud data security strategy?
🔹Did your organization adapt security governance into the cloud?
🔹Is everyone in the team aware of their responsibilities concerning cloud security?
🔹Do you have in-company guidance on how to remain secure within the cloud infrastructure?
🔶Encryption
🔹Have you determined what files, databases, and networks require encryption?
🔹Is all key data on your servers encrypted?
🔹How many encryption services do you have? Do you use a different service for databases, files,
certificates, and public keys?
🔹How you are managing your crypto key (KMAS or BYOK)?
🔶Security updates
🔹How often do you install security updates and patches?
🔹Does the IT team test security updates before deploying them?
🔹Can you do a rollback change to the security systems in case of an emergency?
🔹Does the security team scan the system for vulnerabilities regularly?
🔶Monitoring
🔹Can your cloud system log alterations to policy assignments, security policies, and admin groups?
🔹Can you monitor applications that work with sensitive data?
🔹Does the security team manually check the system for potential security breaches?
🔹How long has the monitoring system been in place?
Source: https://lnkd.in/dkbpWi-g
Credit : AnnaDziuba / relevant.software
Disclaimer – This post has only been shared for technology-related educational and knowledge sharing
purposes. Information was obtained from the source above and credited to the author. There is no endorsement of any products or services.
Keep learning 📚 and keep growing 📈






